RTOS Kernel Architecture
For simpler applications, RTOS is usually a kernel but as complexity increases, various modules like networking protocol stacks debugging facilities, and a device I/Os are included in addition to the kernel.RTOS architecture diagram
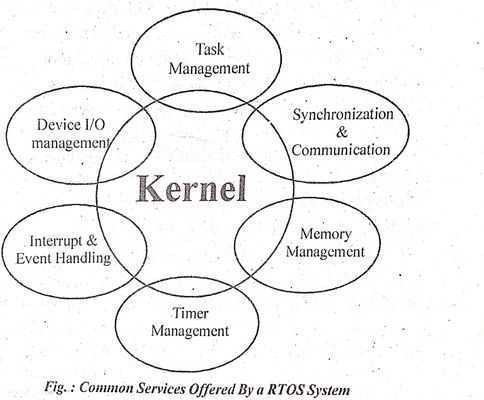
k (A) Kernel, RTOS kernel acts as an abstraction layer between the hardware and the applications. There are three broad categories of kernels
(i) Monolithic kernel
Monolithic kernels are part of Unix-like operating systems like Linux, F FreeBSD, etc. A monolithic kernel is one single program that contains all nine of the code necessary to perform each kernel-connected task. It runs all basic system services (i. e. process and memory management; interrupt handling and Input /Output communication, file system, etc) and provides powerful abstraction§ of the Underlying hardware. The amount of context switches and electronic communication concerning area unit is greatly reduced which makes it runs quicker than a microkernel.(ii) Microkernel
It runs only basic process communication (messaging) and 1/0 control. It normally provides only minimal services such as managing memory protection, Interprocess communication, and process management. The other functions like running the hardware processes are not handled directly by micro kernels. Thus, microkernels provide a smaller set of simple hardware abstractions. It is additional stable than monolithic because the kernel is unaffected even though the servers are unsuccessful (i. e. file system). Microkernels are part of operating systems like AIX, BeOS, Mach, Mac OS X, MINIX, and QNX. etc.
(iii) Hybrid Kernel
Hybrid kernels are extensions of microkernels with some properties of monolithic kernels. Hybrid kernel area unit is similar to microkernels, except that ' they include additional code in kernel space so that such code can run more swiftly than it would be it in the user. space. These are a part of the operative systems like Microsoft Windows NGO, 2000 and XP DragonF 1y BSD, etc.(iv) Exokernel
Exokernels provide efficient control over hardware. It runs only services protecting the resources (i.e. tracking the ownership, guarding the usage, revoking access to resources, etc) by providing a low-level interface for library operating systems and leaving the management to the application.